Real Time Endpoint Protection, Detection, and Automated Response
FortiEDR delivers realtime, automated endpoint protection with orchestrated incident response across any communication device. This service includes workstations, servers, and cloud workloads with current and legacy operating systems, as well as manufacturing and OT systems. The single integrated platform offers flexible deployment options and a predictable operating cost.
- Real Time Proactive Risk Mitigation & IoT Security
- Pre-Infection Protection
- Post-Infection Protection
To open the datasheet, click here.
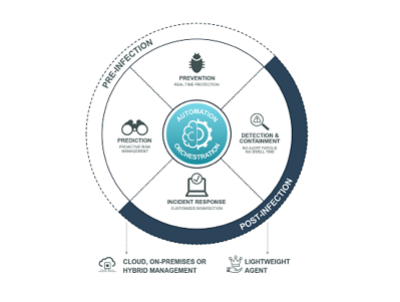
Discover and Predict
FortiEDR delivers the most advanced automated attack surface policy control with vulnerability assessments and discovery
Prevent
FortiEDR uses a machine learning anti-malware engine to stop attacks before execution. This cross-OS NGAV capability is configurable and comes built into the single, lightweight agent, allowing users to assign anti-malware protection to any endpoint group without requiring additional installation.
Detect and Defuse
FortiEDR detects and defuses file-less malware and other advanced attacks in real time to protect data and prevent breaches. As soon as FortiEDR detects suspicious process flows and behaviors, it immediately defuses the potential threats by blocking outbound communications and access to the file system from those processes if and once requested.
Respond and Remediate
Orchestrate incident response operations using tailor-made playbooks with cross-environment insights. Streamline incident response and remediation processes. Manually or automatically roll back malicious changes done by already contained threats—on a single device or devices across the environment.
Investigate and Hunt
FortiEDR automatically enriches data with detailed information on malware both pre- and post-infection to conduct forensics on infiltrated endpoints. Its unique interface provides helpful guidance, best practices, and suggests the next logical steps for security analysts.